Trend Micro CTF Asia Pacific & Japan 2015 Online Qualifier - Offensive 200
This particular challenge was an Android Application. The VirusClicker Application.
The application has a button that you have to click until you reach 10.000.000 clicks and then you should receive the flag.

Looking at the decoded manifest, we could see that there are two activities and one broadcast receiver.
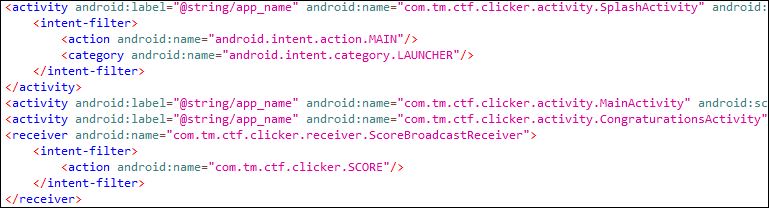
Time to look into the decompiled source code. The code is obfuscated so the task of analyzing the code is a bit more difficult.
The first stop was in the broadcast receiver code located in /com/tm/clicker/receiver/ScoreBroadcastReceiver.class.
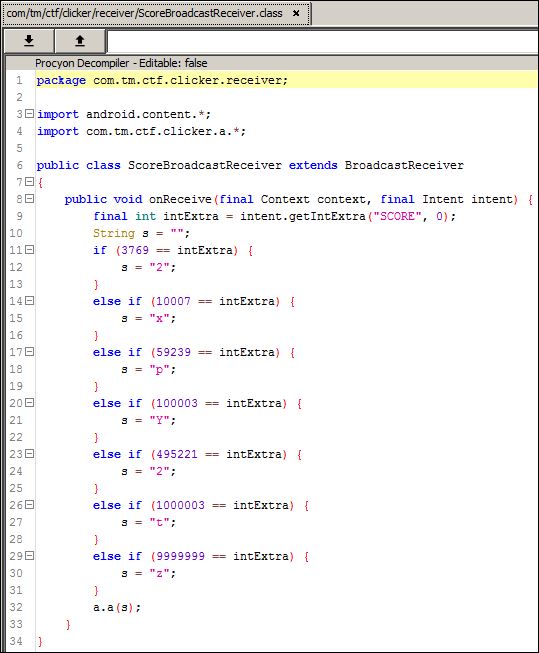
The receiver accepts a integer variable named “SCORE”. Based on that value, some characters are passed to a function on a.a.class.
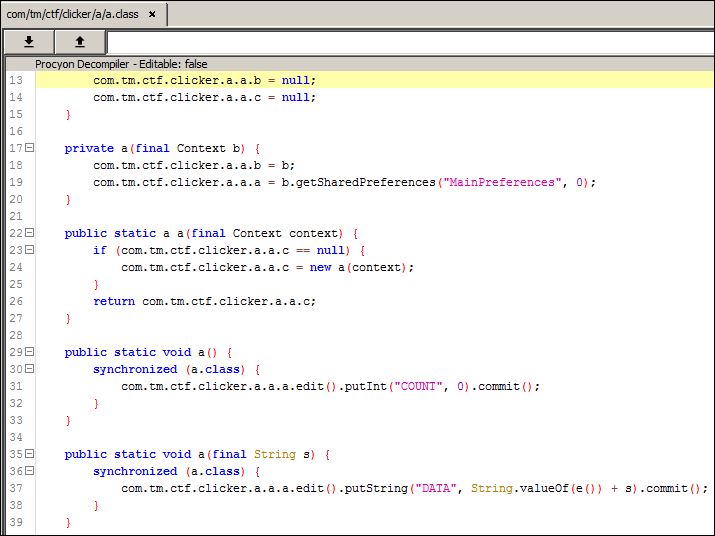
Looking at the class we can see that,that particular method is used to write the characters to a shared preference file MainPreferences in a field called DATA. This file is also used to register the current count of clicks.
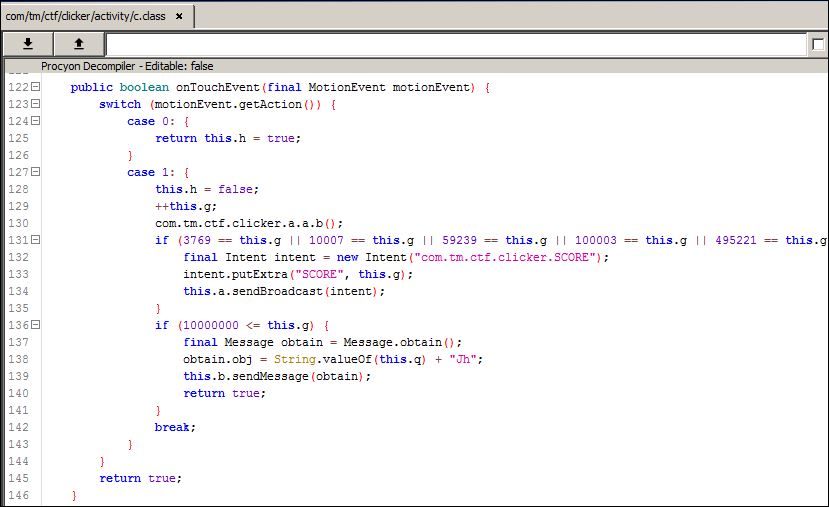
Looking at the c.class, that is the class responsible for the user interface where the actions for clicks are defined, we can see that is where the counter is incremented, the intent is sent for the broadcast receiver. Another interest part is that when the counter reaches 10.000.000 more characters are added to the files.
Now looking at the activity that is going to show the flag.
The activity is going to use a image file f.png to write the flag and present to the user. If you drill down a little bit you find that those characters are actually base64 that in the final process are going to be decoded. One thing that got my attention was that there is a protection in place on line 47, to close the activity if the counter in the file as not reached 10.000.000
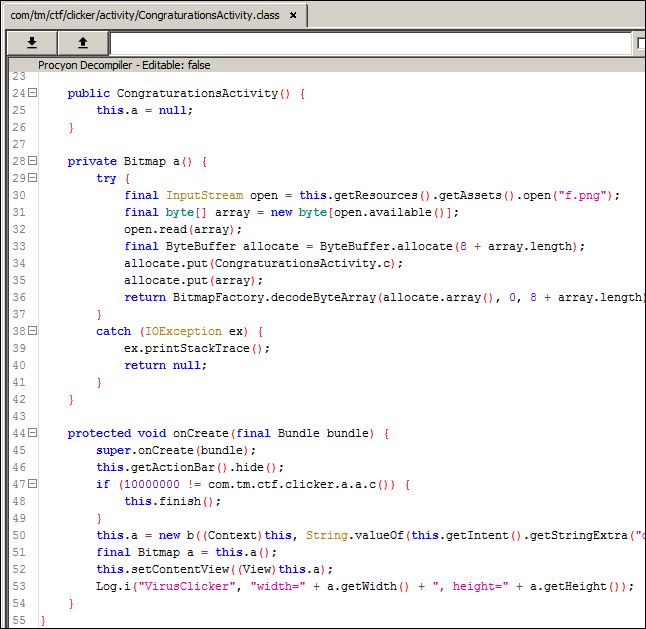
So with this analysed we are certain that we need to reach 10.000.000 so that all the base64 values are appended.
So my approach was:
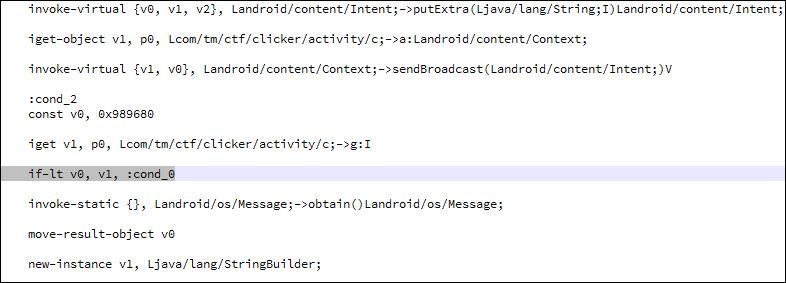
Patch the application in the /activity/c.class to change the condition 10000000 <= this.g to 10000000 >= this.g
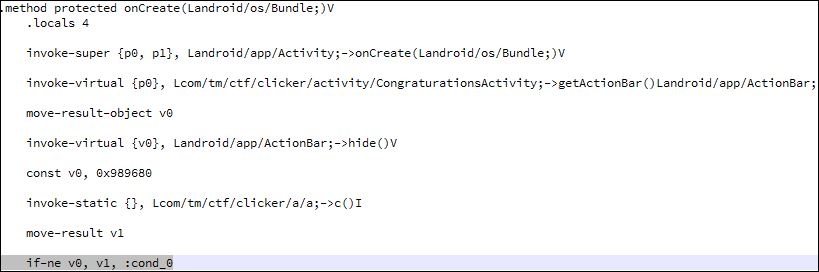
Path the application in the /activity/CongraturationsActivity.class to change the condition 10000000 != com.tm.ctf.clicker.a.a.c() to 10000000 == com.tm.ctf.clicker.a.a.c()
Using apktool to decompile and build the apk again I edited the two classes with the following smali:
CongraturationsActivity.class:
c.class:
With this taken care of we start the application and without clicking the button we use Drozer to the send the following score intents to the broadcast receiver:
run app.broadcast.send –action com.tm.ctf.clicker.SCORE –component com.tm.ctf.clicker com.tm.ctf.clicker.receiver.ScoreBroadcastReceiver –extra integer SCORE 3769
run app.broadcast.send –action com.tm.ctf.clicker.SCORE –component com.tm.ctf.clicker com.tm.ctf.clicker.receiver.ScoreBroadcastReceiver –extra integer SCORE 10007
run app.broadcast.send –action com.tm.ctf.clicker.SCORE –component com.tm.ctf.clicker com.tm.ctf.clicker.receiver.ScoreBroadcastReceiver –extra integer SCORE 59239
run app.broadcast.send –action com.tm.ctf.clicker.SCORE –component com.tm.ctf.clicker com.tm.ctf.clicker.receiver.ScoreBroadcastReceiver –extra integer SCORE 100003
run app.broadcast.send –action com.tm.ctf.clicker.SCORE –component com.tm.ctf.clicker com.tm.ctf.clicker.receiver.ScoreBroadcastReceiver –extra integer SCORE 495221
run app.broadcast.send –action com.tm.ctf.clicker.SCORE –component com.tm.ctf.clicker com.tm.ctf.clicker.receiver.ScoreBroadcastReceiver –extra integer SCORE 1000003
run app.broadcast.send –action com.tm.ctf.clicker.SCORE –component com.tm.ctf.clicker com.tm.ctf.clicker.receiver.ScoreBroadcastReceiver –extra integer SCORE 9999999
After sending all the intents, when you do the first click on the app you get the flag on the screen:
